Most Frequent forms of Cyber Attacks Everyone should be aware:
Definition of Cyber Attack:
Digital devices & internet made life easier, but also brought cyber attacks as a challenge in protecting data. Types of attacks & prevention methods will be discussed.
Cyber attack is defined: as unauthorized access to systems/networks by a third party (hacker). Effects: data breaches, financial losses, harm to customer trust & reputation. Solution: cybersecurity. COVID-19 increased the number of attacks. Different types of cyberattacks are to be discussed next.
As cybersecurity professionals strive to identify and close security vulnerabilities, cyber attackers are continually developing new methods to evade detection, bypass security measures, and exploit new weaknesses. The latest cybersecurity threats are taking advantage of the shift to remote work, the increased use of remote access tools, and the adoption of new cloud services. These evolving threats include:
Different Types of Cyber Attacks:
Varieties of cyber attacks exist. Knowing the types makes protection easier. The top ten attacks will be closely examined. Types of attacks:
1. Phishing Attack:
Phishing attacks are a widespread and common form of cyberattack. It is a type of social engineering attack where the attacker impersonates a trustworthy individual and sends fake emails to the victim.
The victim, being unaware, opens the email and clicks on the malicious link or opens the email attachment. By doing so, the attacker is able to gain access to confidential information and account credentials. They may also install malware through a phishing attack, which can cause further harm. During the first quarter of 2022, 23.6 percent of phishing attacks worldwide were directed toward financial institutions. On top of that, web-based software services and webmail accounted for 20.5 percent of attacks making these two the highest-targeted industries when it came to phishing during the examined quarter.
Preventing Phishing Attacks: Steps to Follow:
- Scrutinize emails received
- Look for significant errors like spelling mistakes and format changes from legitimate sources
- Use anti-phishing toolbar
- Regularly update passwords
2. Malware Invasion/Attack:
Malware attack is a widely-occurring type of cyber attack. It encompasses different malicious software such as worms, spyware, ransomware, adware, and trojans, all collectively referred to as "malware."
One such example is the trojan virus, which hides as legitimate software. Another example is ransomware, which obstructs access to the network's essential components. Spyware, on the other hand, steals the user's confidential data surreptitiously. Lastly, adware displays advertising content like banners on the user's screen.
Malware infiltrates a network through vulnerabilities, which can be triggered by clicking a harmful link, downloading an email attachment, or using an infected pen drive.
Preventing Malware Attacks: Steps to Follow:
Preventing malware attacks requires adopting a few essential measures:
- Antivirus software: Installing antivirus software is the first step in protecting your device from malware. Some popular antivirus software includes Avast Antivirus, Norton Antivirus, and McAfee Antivirus.
- Firewalls: Firewalls serve as a barrier between your device and the internet by filtering the traffic that may enter your device. Both Windows and Mac OS X have built-in firewalls, namely Windows Firewall and Mac Firewall.
- Caution and Updates: Staying alert and avoiding clicking on suspicious links helps to prevent malware infections. Additionally, regularly updating your operating system and browsers helps to ensure that your device is protected against newly discovered vulnerabilities.
3. Man-in-the-Middle Attack:
A Man-in-the-Middle (MITM) attack, also known as an eavesdropping attack, is when an attacker intercepts communication between a client and host. The attacker hijacks the session and steals and manipulates data.
In a MITM attack, the communication line between the client and server is cut off and instead goes through the hacker.
Preventing Man-in-the-Middle Attacks: Steps to Follow:
- Be cautious about the security of the website you access
- Utilize encryption on your devices to ensure secure communication
- Avoid using public Wi-Fi networks, as they are vulnerable to MITM attacks
- Use secure and encrypted connection methods like HTTPS, SSL, or TLS when sending sensitive information online.
- Keep your software and OS updated to the latest version, to prevent vulnerabilities from being exploited by hackers.
4. Password Attack:
Password cracking is a form of attack where a hacker uses various programs and tools such as Aircrack, Cain, Abel, John the Ripper, Hashcat, etc. to gain access to your password. This can be achieved through different methods such as brute force attacks, dictionary attacks, and keylogger attacks.
Preventing Password Attacks: Steps to Follow:
- Choose a complex password consisting of alphabets, numbers, and special characters.
- Avoid using the same password for multiple accounts.
- Regularly change your passwords to reduce vulnerability to a password attack.
- Do not reveal password hints publicly.
- Enable two-factor authentication (2FA) wherever possible.
- Avoid writing down or sharing your passwords with anyone.
5. Denial-of-Service (DoS)
A Denial-of-Service (DoS) Attack, also referred to as a Distributed Denial-of-Service (DDoS) Attack, is a major concern for businesses. The attack involves flooding a system, server, or network with a massive amount of traffic, overloading its resources and bandwidth.
This results in the website hosted by the targeted server being shut down or slowing down, leaving legitimate service requests unanswered. The DDoS attack specifically occurs when the attacker utilizes multiple hacked systems to carry out the attack.
Preventing Denial-of-Service Attacks: Steps to Follow:
- Monitor network traffic to detect malicious activity.
- Be aware of signs such as slow network performance, frequent website downtime, etc…. and respond quickly.
- Develop an incident response plan, including a checklist, to ensure readiness for a DDoS attack.
- Consider utilizing cloud-based DDoS prevention services.
6. SQL Injection Attack:
SQL injection attacks pose a threat to database-driven websites. They occur when a hacker manipulates an SQL query by injecting malicious code into a vulnerable website's search box, potentially revealing crucial information and allowing the attacker to view, edit, and delete tables in the database and gain administrative rights.
To protect against these attacks, ensure database security and implement secure coding practices such as regularly checking and updating the website's code, validating user input, and avoiding untrusted input.
Preventing SQL Injection attacks: Steps to Follow:
- Implement an Intrusion Detection System (IDS) to monitor and detect unauthorized access to a network.
- Validate user-supplied data to ensure it meets specified criteria and prevent malicious input.
7. Cryptojacking:
Cryptojacking is a type of attack that involves unauthorized access to someone's computer for the purpose of mining cryptocurrency. This attack is related to the use of cryptocurrency.
Cryptojacking is accomplished by infecting a website, manipulating the victim to click on a malicious link, or using online ads with JavaScript code. The mining code runs in the background, making the victim unaware of the attack. The only sign they may notice is a delay in the execution of their computer's processes.
Preventing Cryptojacking attacks: Steps to Follow:
- Keep software and security apps up-to-date to prevent cryptojacking.
- Educate employees with cryptojacking awareness training to detect threats.
- Use an ad blocker to block the primary source of crypto-jacking scripts.
- Install extensions like MinerBlock to identify and block crypto mining scripts.
8. Insider Threat:
An insider threat is a security risk that comes from within the organization and not from a third party. This type of threat can cause significant harm, as the insider has knowledge of the organization's inner workings and access to sensitive information.
Small businesses are particularly vulnerable to insider threats, as their staff often have access to multiple accounts and data. These threats can be motivated by greed, malice, or even carelessness, and are often difficult to predict.
Preventing Insider Threat attacks: Steps to Follow:
- Implement security awareness training to promote a culture of security within the organization.
- Limit access to IT resources based on employees' job roles.
- Educate employees on identifying and reporting insider threats.
9. Watering Hole Attack:
A targeted attack focuses on a specific group of people within an organization, region, etc. The attacker identifies websites that are frequently used by this group and infects them with malware. This malware can then infect the systems of those who use these websites, allowing the attacker to access personal information.
To protect against targeted attacks, it is important to regularly update software and security systems, and to be cautious when using websites or clicking on links. Additionally, organizations can educate their employees on how to spot and avoid these types of attacks.
Preventing Watering Hole attacks: Steps to Follow:
- Keep your software up to date to reduce the risk of vulnerabilities being exploited. Regularly check for security patches.
- Use network security tools to detect watering hole attacks, such as intrusion prevention systems (IPS).
- To prevent watering hole attacks, use privacy-enhancing technologies such as a VPN and private browsing mode. A VPN, such as NordVPN, provides a secure connection to another network over the Internet and protects your online activity.
10. Zero-Day Exploit:
A Zero-Day Exploit is a security vulnerability that is unknown to the vendor or developer. This means that there is no solution available for the vulnerability when it is announced.
When the vulnerability is made public, the vendor notifies users about it, but this also alerts potential attackers. The vendor may take some time to fix the issue, but attackers can target the vulnerability before a patch or solution is put in place. This can result in serious security breaches.
Preventing Zero-Day Exploit attacks: Steps to Follow:
- Regularly check for security updates and implement them as soon as possible.
- Conduct vulnerability scans and assessments to identify potential risks and address them before they can be exploited.
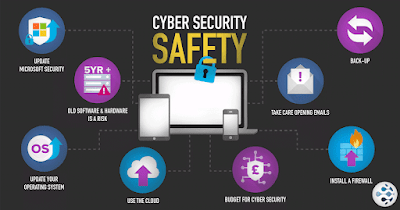
How to Prevent Cyber Attacks:
Let's summarize the ways to prevent different types of cyberattacks discussed and provide some personal tips for avoiding cyberattacks as a whole.
Regularly change strong passwords, avoiding repeating and using complicated ones.
Keep operating systems and apps updated and use a trusted antivirus and firewall.
Be cautious of emails from unknown senders and use a VPN.
Regularly back up data and educate employees on cybersecurity.
Use Two-Factor or Multi-Factor Authentication for added security.
Secure Wi-Fi and mobile devices, only installing apps from trusted sources.
Conclusion:
Understand cyberattacks through this article. Learn about the definition of a cyber attack, the top ten types, and prevention methods. Stay informed about the growing number of cyber crimes and how to protect your network.
FAQs:
Q1. What are Cyber Attacks?
Ans. Cyber attacks are unauthorized access to a system/network by a third party with the aim of destroying or stealing confidential information from a computer network, information system, or device. The attacker is commonly known as a hacker.
Q2. What are the types of attacks?
Ans. Some common types of attacks are:
- Phishing attacks
- Ransomware attacks
- Malware attacks
- Denial of Service (DoS) attacks
- SQL injection attacks
- Man-in-the-middle (MITM) attacks
- Command and Control (C&C) attacks
- Distributed Denial of Service (DDoS) attacks.
Q3. What are some examples of Cyber Attacks?
Ans. Examples of cyber attacks include Twitter celebrity profile hacks, malware-laden emails with attachments, malicious links in emails, and communication streams with harmful packets.
Q4. What are the Methods to avoid Cyber Attacks?
Ans. Ways to prevent Cyber Attacks include updating software, using strong passwords, being cautious of emails from unknown sources, using a VPN, regularly backing up data, educating employees on cybersecurity, enabling Two-Factor or Multi-Factor Authentication, securing Wi-Fi and mobile devices, and only installing apps from trusted sources.
Q5. What occurs during a Cyber Attack?
- Disable, destroy, disrupt, or control computer systems
- Alters, manipulates, blocks, deletes, or steals data
- Carried out by individuals or groups via the internet
- Uses one or more attack strategies
- Causes financial loss of money or theft of information.





No comments:
Post a Comment